North Korean IT Infiltrator Caught via Keystroke Latency Detection at Amazon
- Aisha Washington

- Dec 19, 2025
- 6 min read

The modern corporate perimeter is porous, but sometimes the most sophisticated threats are caught by the simplest mathematical anomalies. Amazon recently revealed that a suspected North Korean IT infiltrator was flagged not by malware signatures or botched code, but by the speed of their typing. Specifically, a consistent, robotic delay in data transmission.
Security teams identified a specific keystroke latency detection pattern—a 110-millisecond lag—that unraveled a scheme involving stolen American identities, domestic laptop farms, and foreign agents attempting to siphon wages back to a sanctioned regime. This incident highlights a shift in cyber warfare where the goal isn't just data theft, but direct employment fraud.
Real-World Solutions: Recognizing the North Korean IT Infiltrator

Before dissecting the Amazon case, we need to address how security practitioners and hiring managers are currently identifying these threats. The North Korean IT infiltrator playbook relies on volume, meaning the mistakes they make are often repeatable.
Based on industry data and the operational security failures seen in recent months, detection relies on triangulating physical hardware with digital behavior.
Implementing Keystroke Latency Detection in Interviews
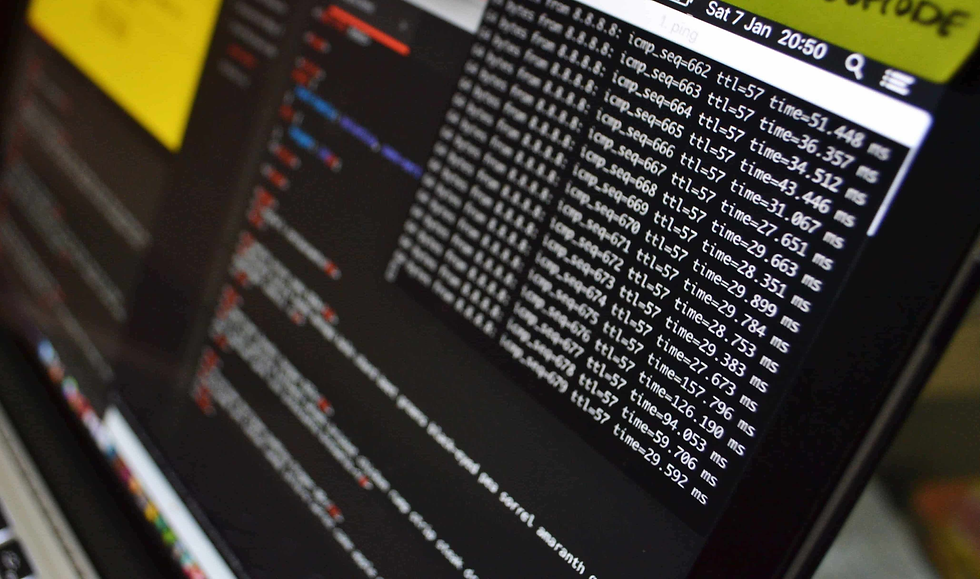
The 110ms lag discovered by Amazon wasn't a fluke; it's a byproduct of the tools used to route traffic. When a worker in Pyongyang or China connects to a laptop sitting in an Arizona living room (a "laptop farm"), the signal passes through multiple tunnels.
The tell: Human typing has a variable rhythm (bursts). Remote desktop protocols (RDP) or KVM (Keyboard, Video, Mouse) over IP setups often buffer inputs, creating a uniform delay.
The solution: Deploy endpoint monitoring that separates network lag (ping) from hardware input lag. If the network is fast but the keystroke registration is consistently slow, you are likely looking at a proxy user.
Biological and Environmental Verification
Technical controls fail if the human element is compromised. Security teams are now advising "liveness" checks that go beyond a simple Zoom call.
The Bait-and-Switch: A common tactic involves a fluent English speaker doing the interview, while the actual North Korean IT infiltrator does the work.
Counter-tactic: Require the camera to be on during unannounced check-ins. Listen for audio artifacts that don't match the claimed location (e.g., sirens or birds that don't exist in that timezone).
Identity Audits: Cross-reference the shipping address for IT equipment. If a candidate claims to live in a luxury apartment in Texas but asks for the laptop to be shipped to a freight forwarder or a residential address in a completely different state associated with known "mules," pause the offer.
Behavioral Red Flags in Code and Communication
The North Korean IT infiltrator often struggles with cultural nuances despite technical proficiency.
Language Syntax: Look for unnatural phrasing in chat logs, specifically the misuse of articles ("a/the") or stiff, archaic idioms that a native US worker wouldn't use.
Work Outsourcing: Evidence suggests these infiltrators sometimes outsource their assigned tasks to cheaper freelancers in other regions to maintain the illusion of productivity. If a senior developer's commit style changes drastically week-to-week, it warrants a code stylometry review.
The Amazon Case: A Victory for Keystroke Latency Detection

The incident at Amazon serves as a textbook example of "active hunting." The company didn't wait for a data breach alert; they were looking for anomalies in the baseline data of their remote workforce.
The 110ms Input Lag Anomaly
Stephen Schmidt, Amazon’s Chief Security Officer, detailed how his team spotted the threat. The actor appeared to be a standard remote employee based in the United States. However, the security telemetry on the laptop showed a persistent gap between the key press and the system registration.
This wasn't just "lag." It was a uniform 110ms input lag anomaly. A normal internet connection fluctuates. A script or a high-end remote management tool trying to synchronize a video feed with keystrokes often creates a flattened, predictable latency curve to prevent jitter. This artificial smoothness flagged the user.
From Digital signal to Physical Arrest
The keystroke latency detection led investigators to the physical location of the device. While the digital worker was likely thousands of miles away, the laptop was physically located in an illicit "laptop farm" in Arizona.
This facility was managed by a U.S. national acting as a facilitator. This woman hosted multiple devices in her home, keeping them powered on and connected to domestic residential Wi-Fi to fool geolocation filters. She has since been convicted for her role in the scheme. This physical component is critical: the North Korean IT infiltrator needs a local accomplice to plug in the hardware.
Since April 2024, Amazon reports thwarting over 1,800 similar attempts, with the frequency of these attacks rising by 27% quarter-over-quarter.
How the "Famous Chollima" Operates
Security firms like CrowdStrike and Microsoft track these groups under various monikers, with "Famous Chollima" being a prominent designation for North Korean state-sponsored actors. Their operations have evolved from pure hacking to revenue generation.
The Infrastructure of Remote Desktop Identity Fraud
The operation is distinct from traditional hacking. The goal isn't destruction; it's a paycheck.
Identity Acquisition: They purchase or steal identities of real U.S. citizens.
The Farm: They pay a U.S. resident to host the corporate laptop.
The Tunnel: They use software like Anydesk, TeamViewer, or proprietary KVM-over-IP hardware to control the laptop remotely.
This infrastructure is why keystroke latency detection is effective. You cannot break the laws of physics. Routing a signal from Pyongyang to China, through a VPN, to an Arizona residential IP, and then to Amazon's corporate network introduces unavoidable latency. To make the work experience usable, the software compensates by buffering, creating the detectable 110ms fingerprint.
Economic Motivation
The U.S. Department of Justice and FBI have seized multiple domains and devices associated with these rings. The wages earned by a single North Korean IT infiltrator—often reaching six figures annually—are funneled back to the regime to circumvent sanctions and fund weapons programs. It is a state-level revenue stream disguised as the gig economy.
Analyzing the Blind Spots in Remote Work

The Amazon success story also exposes a gap in standard enterprise defense: reliance on IP reputation.
Most corporate VPNs checks simply ask: "Is this login coming from a U.S. IP address?" Since the laptop farms use legitimate residential ISPs (like Comcast or AT&T) in actual American homes, they pass this check every time.
Keystroke latency detection works because it ignores the IP address and looks at the hardware behavior. Organizations relying solely on Geofencing are currently defenseless against this specific threat vector. The proxy isn't digital; it's physical.
Furthermore, the "Famous Chollima" actors are exploiting the social contract of remote work. Privacy laws in the EU and strong employee advocacy in the US make companies hesitant to install invasive monitoring software. However, the legal distinction is clear: on company-owned equipment, there is no expectation of privacy regarding performance metrics like input timing.
Strategic Defense: Beyond the 110ms Lag
While keystroke latency detection is a powerful tool, it is not a silver bullet. Attackers will adapt. They will improve their compression algorithms or move physically closer to the target regions if possible.
To maintain security against the North Korean IT infiltrator, companies must adopt User Entity Behavior Analysis (UEBA).
Moving to UEBA Security Tools
Static rules (like "block North Korean IPs") are obsolete. UEBA builds a profile of how a specific user acts.
Time of Day: Does the user consistently work during hours that align with daylight in East Asia, despite being "based" in Texas?
File Access Patterns: A software engineer siphoning code repositories often accesses files differently than one who is contributing code.
Application Usage: Are they running virtualization software or remote admin tools that aren't part of the standard developer stack?
The "Active Hunting" Mindset
Amazon’s Chief Security Officer noted that they found these actors because they were looking for them. Passive alerts did not trigger. Security Operation Centers (SOCs) need to dedicate cycles to hypothesis-based hunting.
One specific hypothesis to test is the "Impossible Traveler" scenario tailored for VPNs. If a user's keystroke characteristics match a high-latency connection, but their network jitter reports a high-speed fiber connection, the discrepancy suggests traffic manipulation.
By layering keystroke latency detection with rigorous physical identity verification and behavioral analysis, organizations can dismantle the laptop farms that facilitate this fraud. The 110ms delay was a small error in a massive operation, but it pulled the thread that unraveled the entire sweater.
FAQ: Detecting Insider Threats
What exactly is the 110ms input lag anomaly?
It is a consistent delay between a user pressing a key and the character appearing on the screen. In the Amazon case, this specific 110ms delay indicated the use of remote desktop software buffering data over a long distance, rather than a direct human-to-computer interaction.
How does a North Korean IT infiltrator pass a video interview?
They often use "front" candidates—fluent English speakers who sit for the interview. Once hired, the actual worker takes over the credentials. Alternatively, they may use deepfake video technology or claim camera malfunctions to obscure their identity.
Why is Keystroke Latency Detection more effective than IP blocking?
IP blocking fails because the attackers use "laptop farms" located within the United States using legitimate residential internet. Keystroke latency detection analyzes the behavior of the hardware itself, which cannot be easily spoofed without physical proximity.
What is a "laptop farm" in the context of IT fraud?
A laptop farm is a physical location, usually a residential home in the US, where a facilitator hosts dozens of corporate laptops sent to remote employees. The facilitator keeps the laptops powered on and connected to the internet, allowing overseas actors to remote into them.
What are the primary indicators of remote identity fraud?
Key indicators include consistent high latency in inputs, discrepancies between declared location and audio background noise, inability to appear on camera unexpectedly, and payroll accounts linked to digital banks or freight forwarding addresses.


